We don’t receive a lot of these kinds of messages from SonicWALL so when it came in it was treated with much suspicion.
The message can be found here: SonicWALL Security Advisory Announcement
Below is a quote with all of the tracking stuff removed from the URLs.
July 19, 2019
A message from Bob VanKirk, SVP and Chief Revenue Officer
Dear Philip,
Ensuring the security of our customers is a responsibility we take seriously at SonicWall and we work vigilantly to always keep our customers secure. To that end, I wanted to make you aware of the security advisory we released today. We will be communicating this information to our end users as well and posting messaging on our support and product notification pages. We have also developed materials that should be helpful to you and SonicWall end users, including step-by-step text and video instructions on how to update your SonicOS Firmware. Should you or a customer need immediate technical support, please open a support case online.
Mitigation Steps
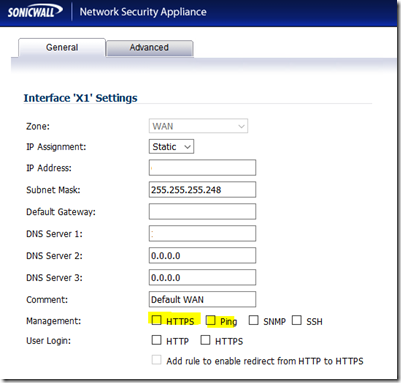
For now, get in there and disable management on the X1 (WAN) interface.
- Log on to the admin portal from _inside_ production/management network
- Click on Network
- Click on Interfaces (usually comes up by default)
- Click the Edit button to the right of X1
- B
- Remove any tick marks from HTTP and HTTPS
- Click OK
- Log off
Note that it does not matter what port the management portal is listening on, someone would find it!
As an alternative, one could set up a Firewall rule set that allows only our office IP address to have access to that port on the WAN interface. Normally, the only time we open this setting up is when we’re troubleshooting a firewall rule that does not seem to be working as expected.
A Rule of Thumb or Two
- Never, ever, open a management interface to the Internet unrestricted. Never
- iDRAC, iLO, Intel RMM, any other such device included
- Update all edge devices. Pay for the support if need-be but keep them up to date.
Conclusion
We are in the process of checking all of our managed SonicWALL firewalls to make sure they are not accessible and are up to date.
Note that the SonicWALL site was offline for most of this morning. Co-incidence with the announcement? Not sure.
That being said, being safe is better than being sorry. 😉
Philip Elder
Microsoft High Availability MVP
MPECS Inc.
www.s2d.rocks !
Our Web Site
Our Cloud Service